Cybersecurity Tips to Protect Your Wealth
Feb 4, 2024As the financial industry becomes increasingly reliant on technology, digital transactions, and online banking, managing one’s personal finances has never been easier. There are added risks that come with this convenience, however, and ensuring the security of one’s personal finances has become more critical than ever. Thankfully, financial institutions are investing in cybersecurity and taking measures to safeguard their clients’ assets. At the same time, institutions alone cannot ensure total security, as individuals play a crucial role in protecting their digital safety. Please implement the following cybersecurity tips to ensure your finances are protected:
1. Create strong and unique passwords
- One of the simplest, most effective ways to enhance cybersecurity is by using strong, unique passwords for financial accounts.
- Avoid repeating passwords and opt for a combination of upper and lowercase letters, numbers, and special characters.
- Consider using a reputable password manager to generate and store complex passwords securely. Examples include:
- Dashlane
- 1Password
- Bitwarden
- This need for strong passwords also applies to home Wi-Fi networks, which can be an entry point for cybercriminals.
2. Enable two-factor authentication
- Two-factor authentication is an additional layer of security that requires a second form of authentication in addition to a password.
- Two-factor authentication typically involves receiving a one-time code to a mobile device or email that must be entered to access the account.
3. Regularly update software and applications
- Ensure that computer software and mobile device applications are regularly updated or set up automatic updates wherever possible.
- Updating software and applications regularly provides critical security enhancements.
- If outdated, software and applications may be susceptible to security threats.
4. Beware of phishing attempts
- Phishing is one of the most common types of cyberattacks and is the practice of sending fraudulent communications that appear to come from a legitimate and reputable source, usually through email, phone calls, or text messaging.
- This practice involves deceiving, pressuring, or manipulating people into sending assets or personal information to the wrong place.
- The attacker typically disguises themselves as a person or organization the victim trusts and creates a sense of urgency to encourage the targeted person to act quickly.
- Example of a phishing email:
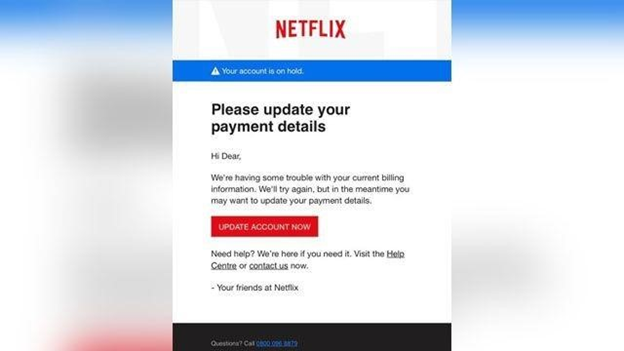
*Source: Federal Trade Commission Consumer Advice
-
- At first glance, this email appears to be real, but here are some signs this is a scam:
- The email has a generic greeting.
- The email says the account is on hold due to a billing issue.
- The email prompts the user to click a link and enter financial information.
- At first glance, this email appears to be real, but here are some signs this is a scam:
- How can you identify and protect sensitive information from phishing attacks?
- If an email or text message prompts the user to click on a link or open an attachment:
- The user should determine whether they have an account with the company or know the person who contacted them.
- If not, it could be a phishing scam and the user should delete the message.
- If yes, the user should contact the company directly, using a website or phone number that is real and verified, not the information in the email.
- The user should determine whether they have an account with the company or know the person who contacted them.
- Review the sender’s email address.
- Does the sender’s email address appear to be legitimate and representative of the website it claims to be from?
- Are there any noticeable errors in grammar or spelling?
- If an email or text message prompts the user to click on a link or open an attachment:
- If one already responded to a phishing email:
- If the user believes a scammer has their personal information, such as Social Security number, credit card, or bank account, visit www.identitytheft.gov for best next steps.
- The user should run a security scan and remove anything the security software identifies as a problem. Here are some examples of security software:
- Microsoft Defender
- Norton
- McAfee
- How to report a phishing attempt:
- If one suspects a phishing attempt, they should report it, as this information helps fight scammers.
- For phishing emails, forward to the Anti-Phishing Working Group at reportphishing@apwg.org.
- For phishing text messages, forward to SPAM (7726).
- Report the phishing attempt to the Federal Trade Commission (FTC) at www.Reportfraud.ftc.gov.
- If one suspects a phishing attempt, they should report it, as this information helps fight scammers.
5. Monitor financial statements and activity
- Regularly review bank and credit card statements to help detect any unauthorized or suspicious activity.
- Most major banks offer real-time transaction and fraud alerts, which can be enabled by the account owner.
- If there are any discrepancies or alerts, contact the financial institution immediately.
As our financial lives have become reliant on technology, prioritizing cybersecurity has become more essential than ever for both institutions and individuals. These cybersecurity tips are an important foundation to help individuals stay vigilant and protect their wealth. At Glassy Mountain Advisors, we’re here to help. For questions about these financial cybersecurity tips, please contact Matt Altman (maltman@glassymountainadvisors.com).




